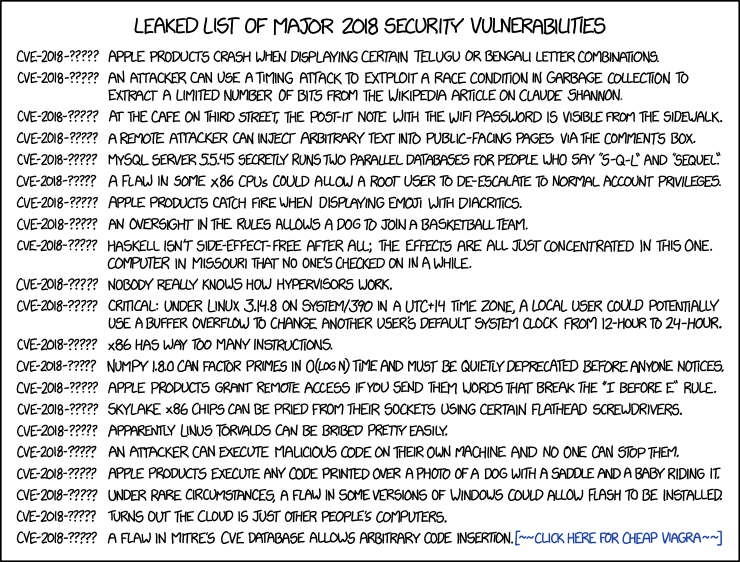
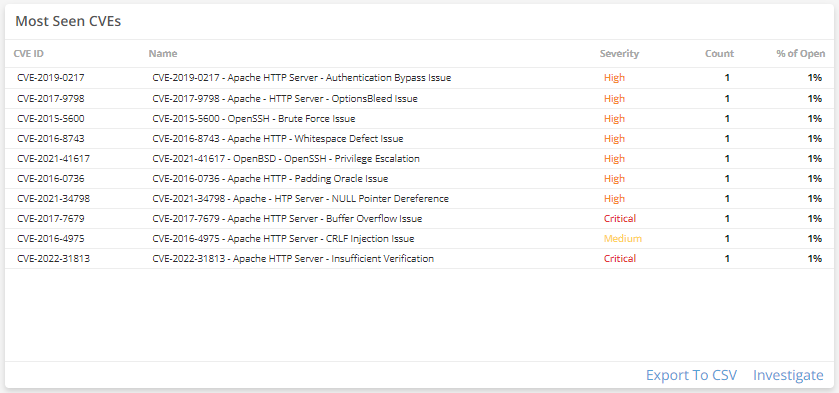
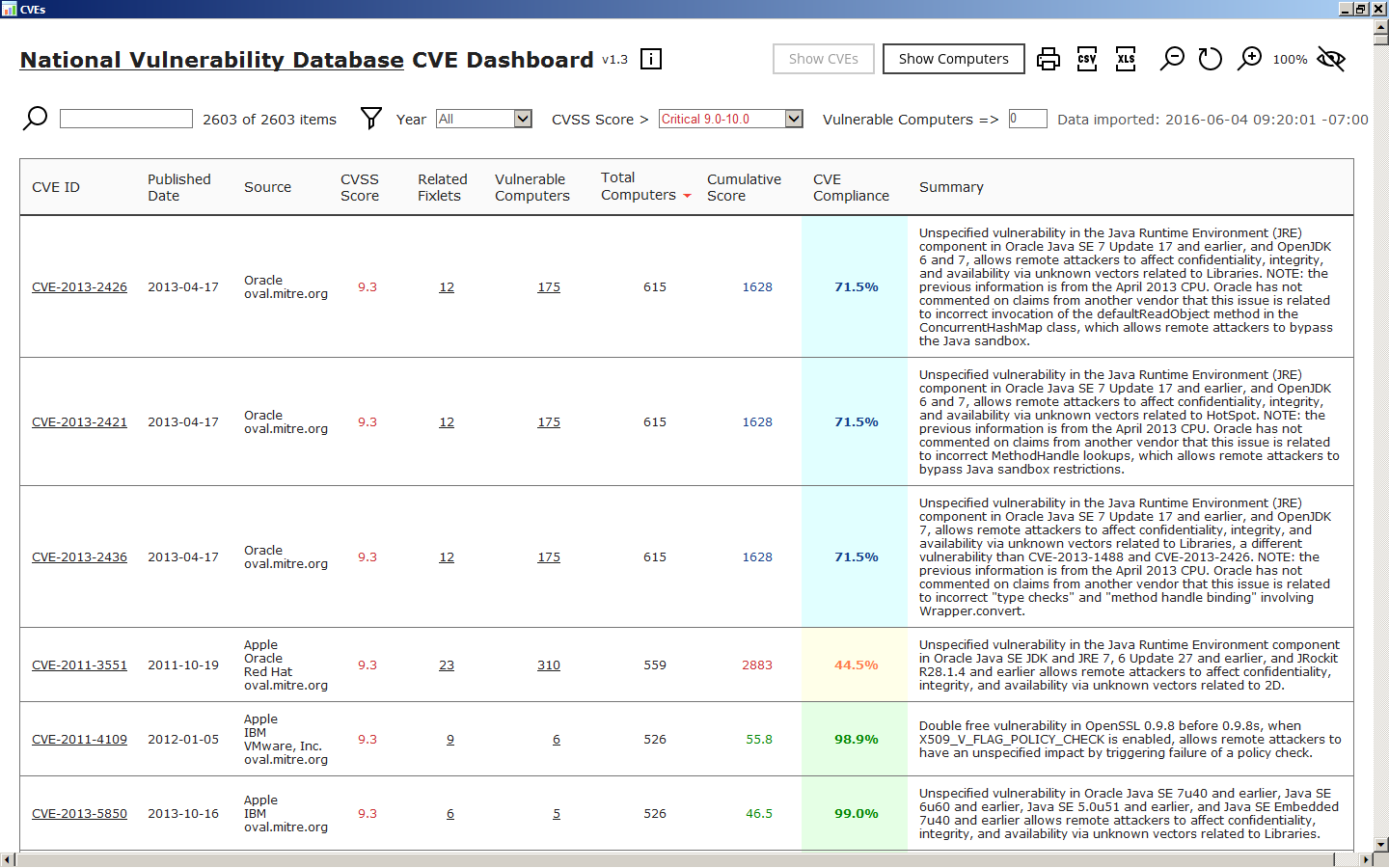
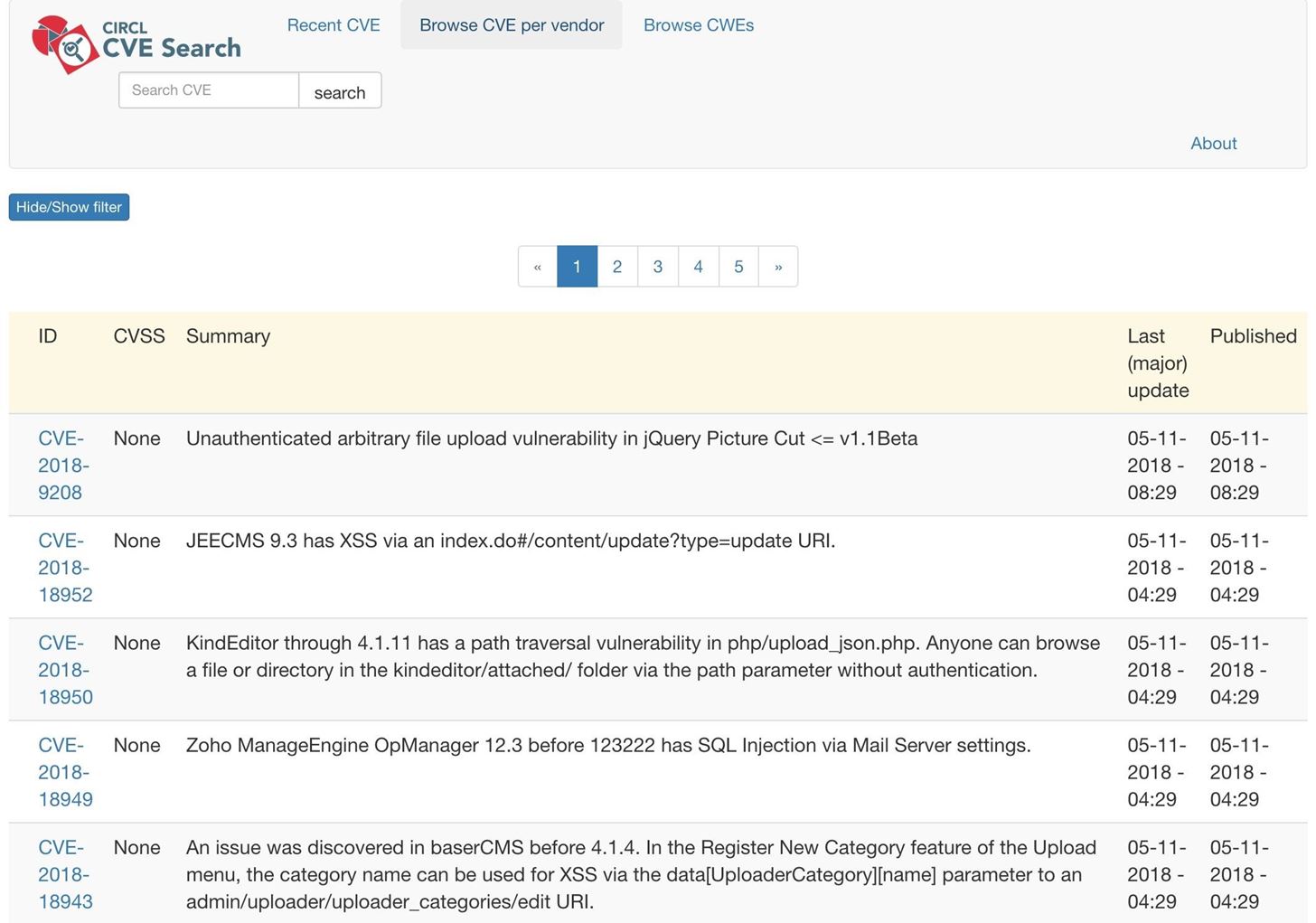
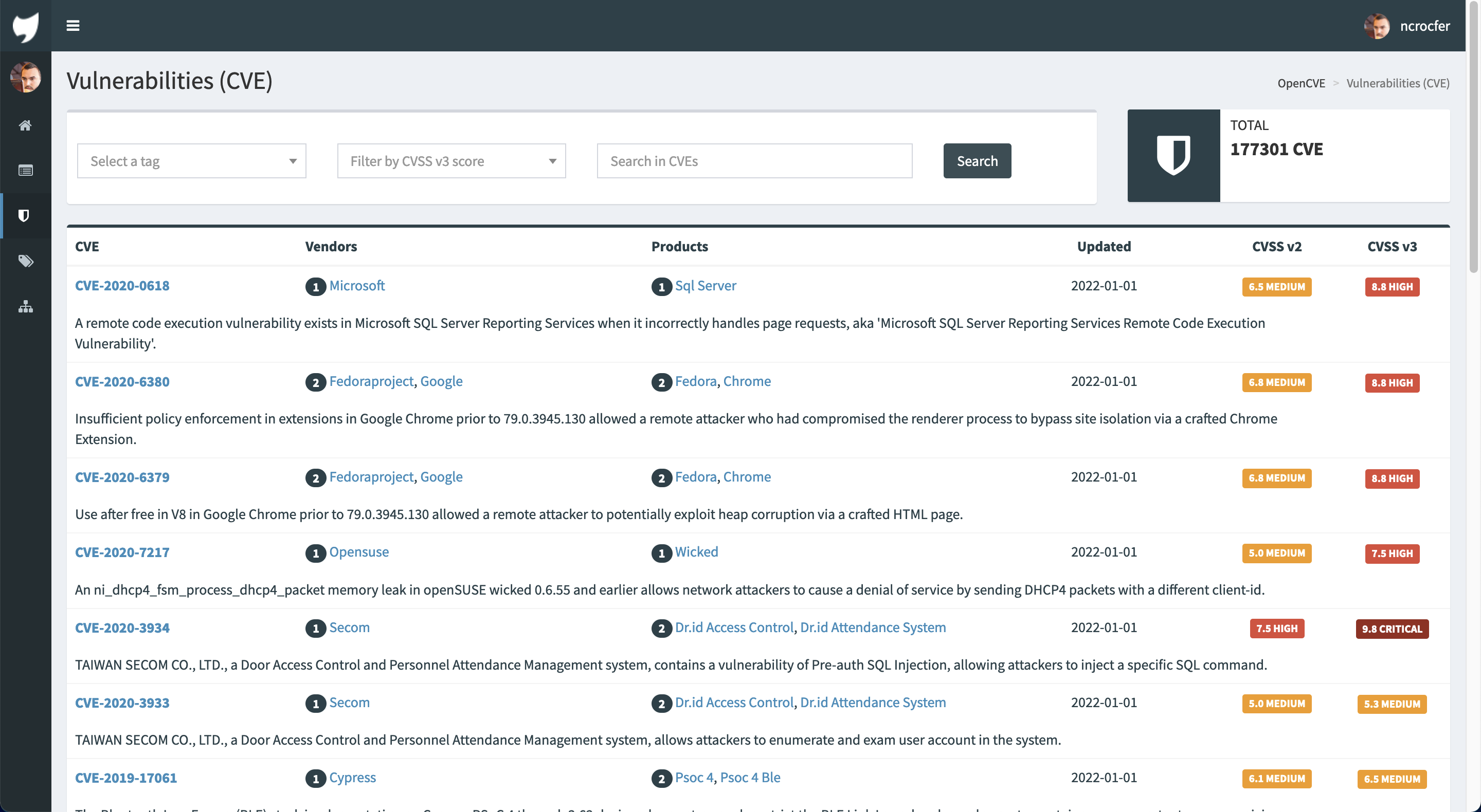
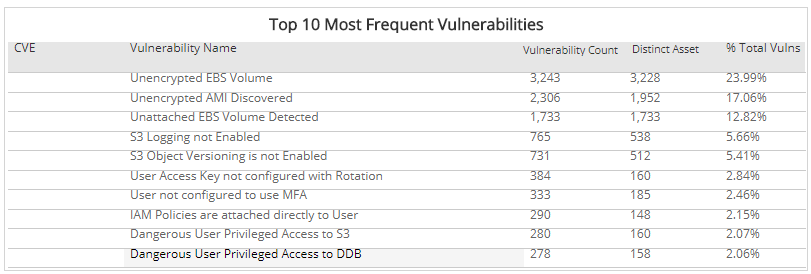
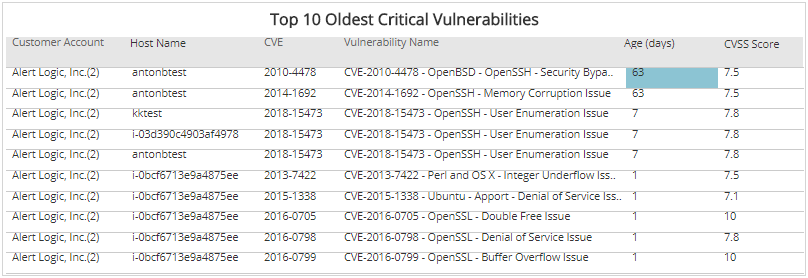
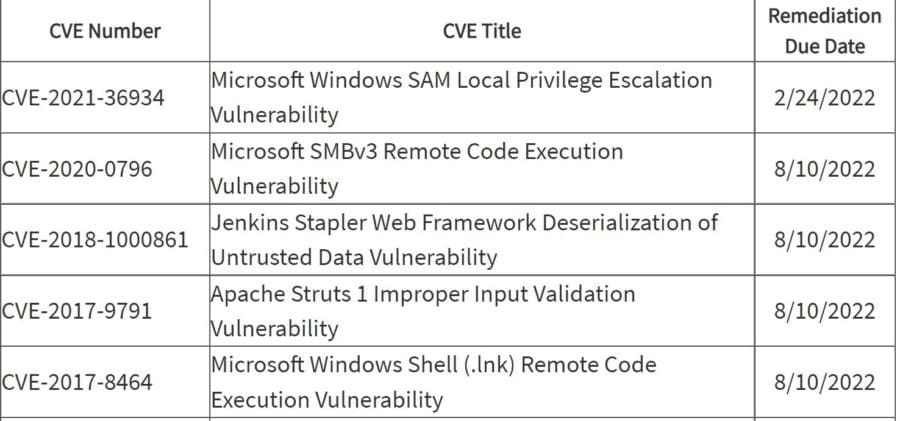
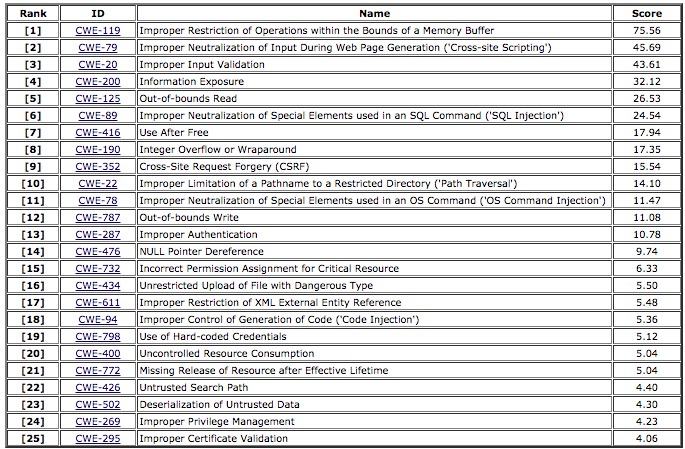
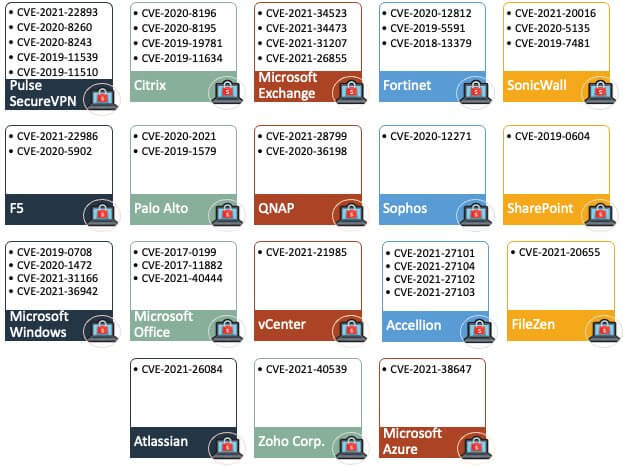
Some information regarding Freak Attack - CVE-2015-1637 - TechNet Articles - United States (English) - TechNet Wiki
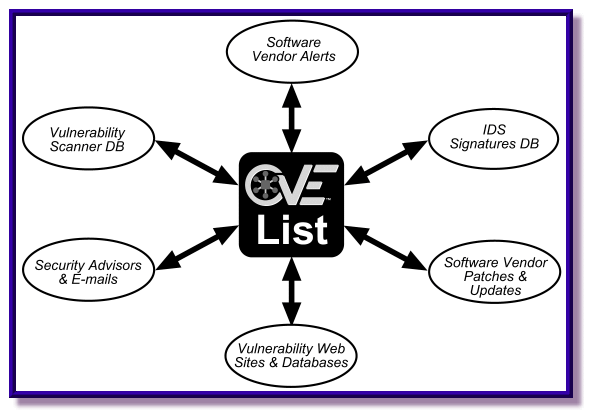
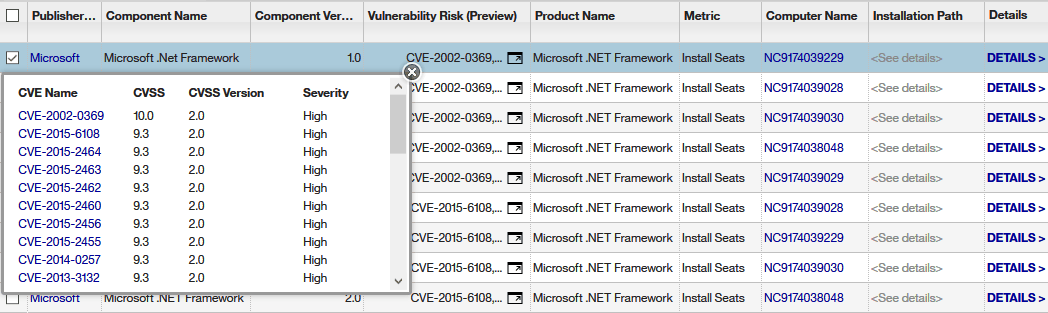
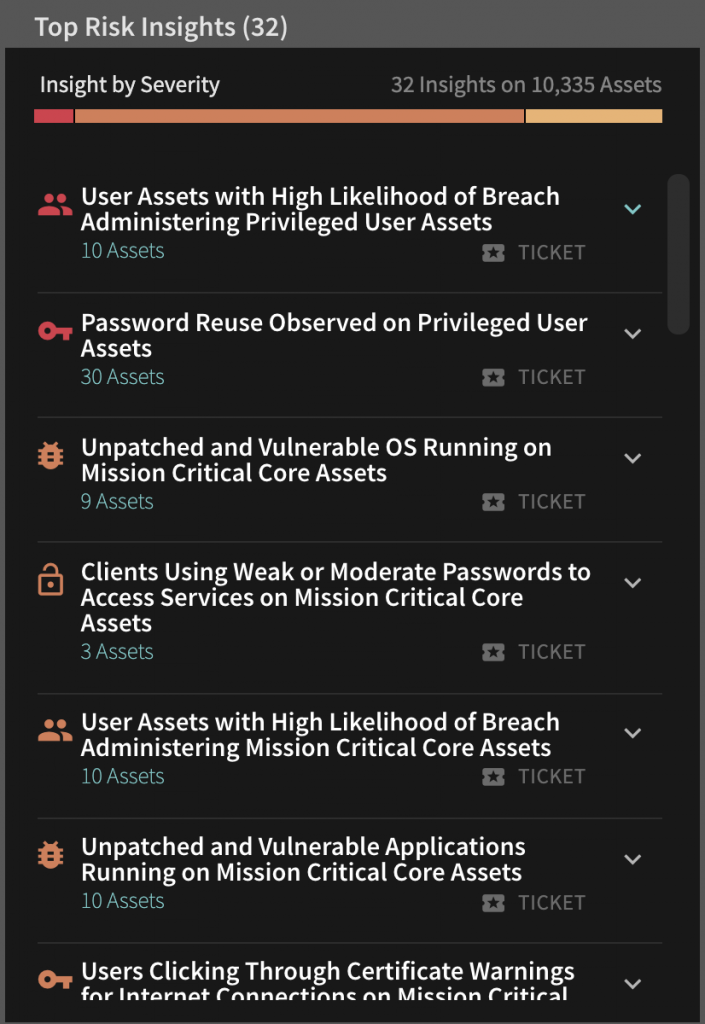
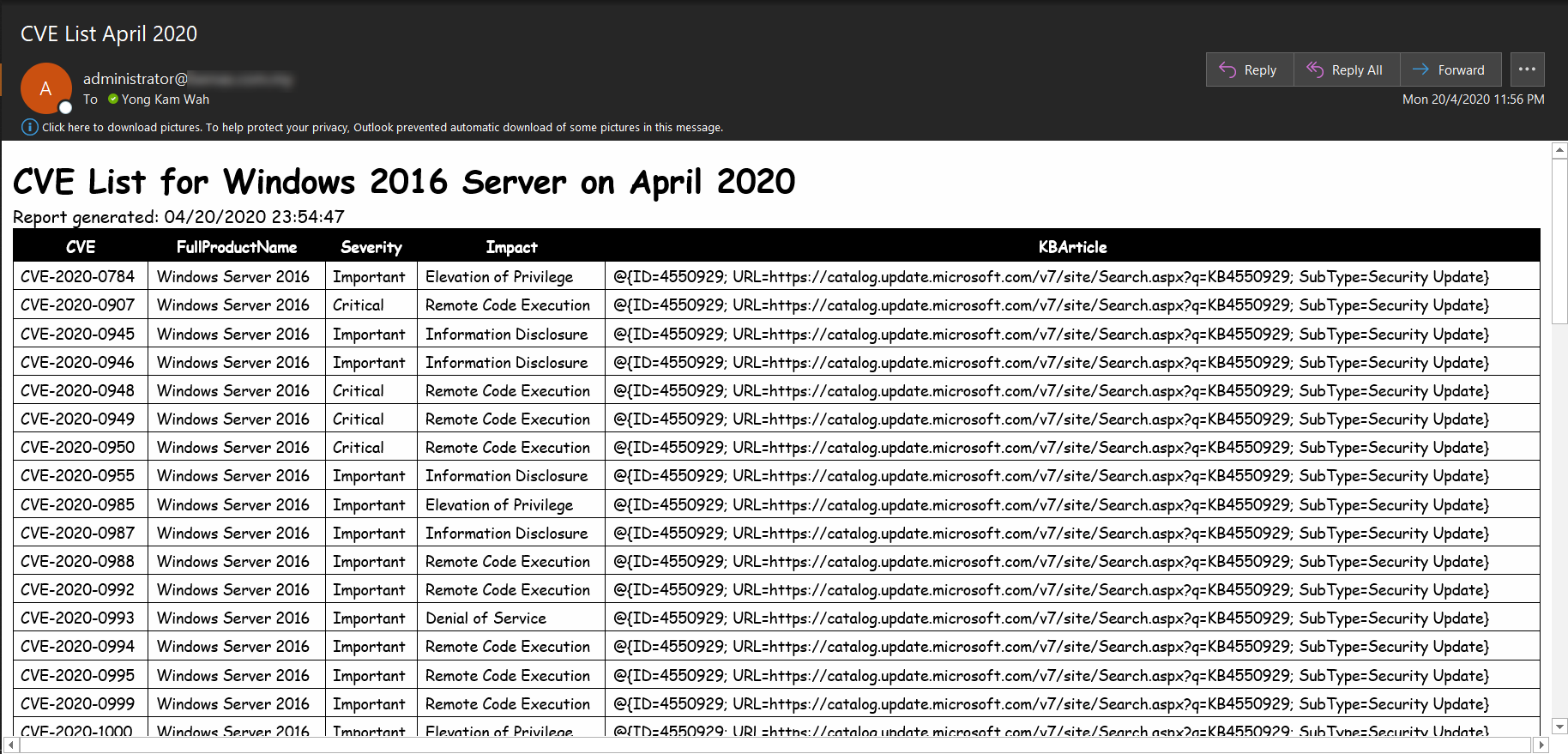
Adventures in Automation: Introduction to Vulns, Common Vulnerabilities and Exposures, the CVE List, and the National Vulnerability Database